Attackers nearly gained immediate access to certain Linux machines running an infected distribution, marking what could have been one of the most significant supply chain attacks ever discovered. The scale of this threat cannot be overstated. If these malicious packages had infiltrated most of the world’s Linux releases, it would have sparked a security nightmare – and it came dangerously close to doing so. The affected Linux distributions included Kali Linux (between March 26th – March 29th), Fedora 40, 41, and Fedora Rawhide (the current development version of Fedora Linux).
The attack we are referring to is the compromise of ‘XZ Utils’, a widely used data compression format found in almost every Linux distribution, across community projects and commercial product distributions. It allows for compression and decompression of large file formats into smaller, more manageable sizes for efficient file transfers.
One of the main developers of XZ Utils known as “JiaT75”, or “Jia Tan” orchestratedthe compromise which could have caused chaos. With years of legitimate contributions to the project, Jia strategically infiltrated his way into a “maintainer” role on GitHub, through seemingly genuine development efforts. However, it now transpires this was part of a sophisticated plan. He used this role as a trusted contributor to gradually introduce malicious, obfuscated code, with legitimate explanations as to not arouse suspicion. This code created a backdoor, enabling a threat actor, with a predetermined private key, to remotely execute malicious commands on infected machines who used the builder of XZ Utils.
Notably, during Jia’s journey to reach maintainer status, two other accounts complained about slow updates. These accounts were likely fabricated and aimed at pressuring the first maintainer into assigning a co-maintainer – after Jia had placed himself in the ideal position to be chosen. The dedication and commitment of this attack has led to speculation that it could be state sponsored.
How Was It Discovered?
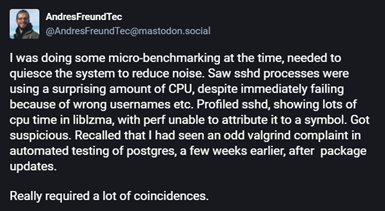
Andres Freund, a PostgreSQL developer, was micro-benchmarking and noticed SSH was taking 500ms longer than usual. After considered investigation, he , eventually uncovered the malicious backdoor. Without his attentiveness, this backdoor may have continued to go unnoticed, and the world could be recovering from one of the worst hacks in its history.
Lessons Learnt
Open-source software does not mean safe software. Without continuously checking each release of the product, there are no guarantees of security. In this case, through chance, the slow release of the packages and the investigative nature of Andres Freund may have prevented catastrophe.