Continuous Monitoring
Businesses are recognising the necessity for up-to-date and proactive cyber security solutions. Modern challenges must be met with modern solutions – requiring us to adapt.
This has led to the emergence of continuous monitoring: a solution made possible by the latest technological advancements in automation that organisations are rapidly adopting. A significant shift from reliance on ad-hoc testing methods, utilising continuous monitoring is an opportunity to gain constant visibility of weaknesses in your IT infrastructure – this was previously unobtainable with point-in-time testing.
Increasing visibility of business controls across an organisation is becoming essential, especially for businesses embarking on ISO 27001 certification. Introducing continuous scanning and monitoring of your key IT security controls provides you with a constant view of your risk, making it simple to remain compliant to security standards and certifications.
A game changer to security testing, continuous monitoring is the automated, daily scanning of systems and networks to detect cyber weaknesses. In recent years, there has been a growing awareness of the limitations of traditional point-in-time cyber security solutions such as penetration testing. These conventional methods leave significant time periods in which a business is susceptible to attack.
Whilst manual penetration testing is imperative, it is essential to recognise that for comprehensive cyber security, incorporating both ad-hoc testing and continuous monitoring is the key to ensuring the protection for your business. A continuous approach is essential to avoid being left in the dark for most of the year. Ad-hoc penetration test results quickly become outdated as new vulnerabilities emerge and remain undetected due to the lack of ongoing monitoring or assessment. This leaves an organisation open to attacks until the next assessment is conducted, which is often up to an entire year later.
This is no longer acceptable – the technology for daily insight exists and is being utilised right now by those who are staying ahead of the curve and are up to date with the latest cyber security strategies.
An analogy that will resonate with most readers is thinking of how your car displays issues. A couple of times a year, you may take your vehicle to the garage for a check-up or an MOT. But for the rest of the year, you retain visibility of issues through the warning light system on your dashboard. Without the warning light system, if you were not knowledgeable about vehicles or regularly performing your own checks, you would be left in the dark. Issues could arise, and you could unknowingly continue driving none the wiser – until the issues lead to breakdown and expensive repairs. With cyber security the concept is the same, except the stakes are higher.
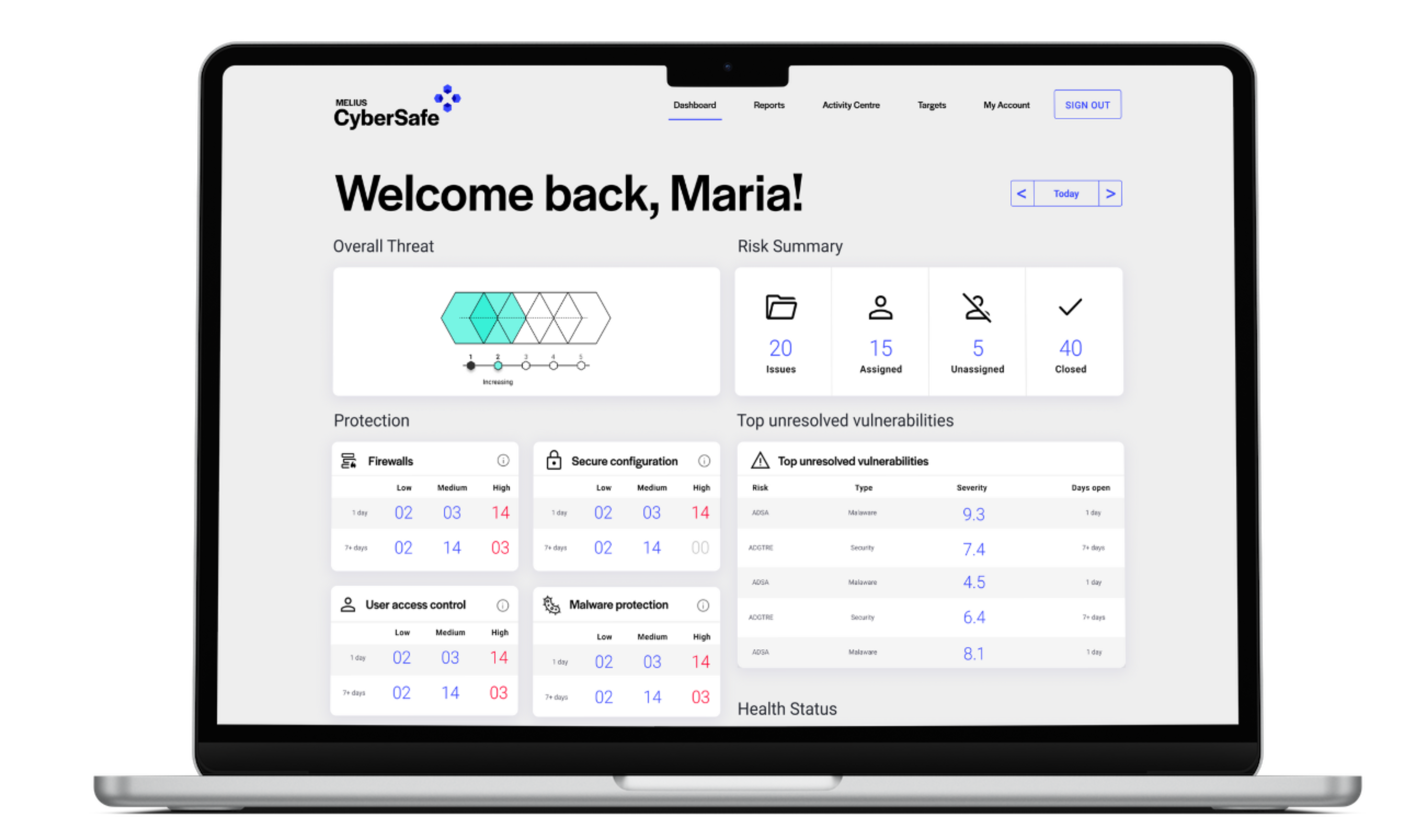

Risk is heavily reduced when you can actively stay on top of security weaknesses all year-round. Furthermore, workload is heavily reduced by spreading out remediation activities over the year – rather than being forced to tackle hundreds at once following a point-in-time test.
Additional Benefits of Continuous Monitoring
• Continuous compliance: staying on top of certification or compliance controls has never been easier. Utilising continuous monitoring ensures that you can see where your business stands regarding controls, at any point in time.
• Proactive approach: vulnerabilities are found and can be remediated before they become a problem.
• Cost-effective: provides you with the information you need to be safe, without the need for expensive alternatives.
• Save time and resources: your IT department does not have to spend a huge amount of time remediating issues when the annual penetration test report comes in. With continuous monitoring, your next penetration test report should be empty – you have kept on top of issues day by day.
A truly proactive solution must be continuous because hackers will not wait for your penetration test. Businesses that use continuous monitoring platforms such as Cyber Safe can rest easy, knowing that they would be alerted immediately if a security weakness arose. Realise that modern technology has given us new ways to approach cyber security, and capitalising on this is not something to miss out on.